Imagine your most private information—personal information, financial records, or trade secrets—resting comfortably within the confines of a virtual vault in a world where digital landscapes are constantly evolving. The strength of data encryption at rest, a security measure that makes your stored data unintelligible to prying eyes, makes this peaceful scenario more than just a dream.
We’re glad you’re here for our in-depth examination of this critical security measure, where we look at the fundamentals of data encryption at rest. We shall explore its complexities throughout this post, highlighting the what, how, and motivations behind this digital barrier.
First, let’s start with the definition of data at rest encryption.
Table of Contents
- What Is Data Encryption?
- What Is Data at Rest?
- What Is Data at Rest Encryption?
- The Purpose of Data at Rest Encryption
- How Data Encryption at Rest Works?
- Encryption at Rest vs In-Transit vs Data in Use
- Types of Data at Rest Encryption
- Importance of Data at Rest Encryption
- Six Best Practices for Data at Rest Encryption
- Data Encryption Trends Types
- Conclusion
- FAQs
What Is Data Encryption?
Credits: Freepik
Data encryption is a technique for securing information by encoding it so that only a person possessing the right encryption key may decrypt or access it. Unauthorized access to encrypted data causes it to look scrambled or unintelligible.
Data encryption changes the original form of the data into a code that can only be accessed with a secret key (formerly known as a decryption key) or password. Data that has been encrypted is known as ciphertext, while data that has not been encrypted is known as plaintext.
Encryption is one of the most popular and effective data protection techniques used today in businesses.
What Is Data at Rest?
Credits: Freepik
Data at rest refers to information that has accumulated in one location. Data in databases, file systems, big data lakes, the cloud, and storage infrastructure, in general, are likely considerably more alluring to hackers than individual data packets traveling across the network.
Credit cards, intellectual property, personal information, healthcare information, financial information, and other types of “money” are typically stored in these settings and have logical structures, meaningful file names, or other telltale signs that they are there.
What Is Data at Rest Encryption?
Credits: Freepik
Data at Rest Encryption is a cybersecurity exercise that helps prevent unauthorized access. Data is converted into ciphertext during encryption, and the decryption key is the sole means to restore the files to their original state.
Unauthorized users with access to encrypted data but lack the decryption key must circumvent encryption to decode the data. Comparing this method to accessing unencrypted data on a hard disc reveals how much more difficult and resource-intensive it is.
Data at rest encryption is essential for data security and lowers the risk of data loss or theft in the following scenarios:
- A breach of data
- Gadget theft or loss
- Accidental password exchange
- Accidental authorization
- Leaking of data
The Purpose of Data at Rest Encryption
Credits: Freepik
Data at Rest Encryption ensures the data is encrypted when stored on a disc, preventing the attacker from accessing the unencrypted data. If an attacker gets their hands on a hard disc containing encrypted data but not the encryption keys, they will need to circumvent the encryption to access the data.
Accessing unencrypted data on a hard drive is more superficial and requires fewer resources than this assault. For this reason, many organizations emphasize the need for data at rest encryption and strongly advise it.
How Data Encryption at Rest Works?
Credits: Freepik
So, how does data encryption at rest work? In this section, we will learn its working procedure with the help of an example.
-
Symmetric Encryption
One popular encryption technique uses symmetric encryption algorithms, which encrypt and decrypt data using the same key. Let’s take a situation where a user maintains private data on a computer’s hard disc, such as financial records.
The data is converted into a scrambled, encrypted version when the user turns on encryption at rest using a particular encryption method and a private key. Anyone attempting unauthorized access will see random, meaningless characters instead of the saved data without the key. The encryption key decodes the data when the user needs to access it, restoring it to a readable state.
-
Asymmetric Encryption
Asymmetric encryption, commonly called public-key cryptography, encrypts and decrypts data using a set of two keys. The set of keys consists of a private key that the owner keeps a secret and a public key that anybody can use.
Asymmetric encryption encrypts data using the recipient’s public key rather than the sender’s. The data is subsequently decrypted by the recipient using their private key. This method enables secure communication between two parties without requiring that they share a secret key.
For instance, if Alice wishes to send Bob a secure communication, she encrypts the message using Bob’s public key. The original message can then be decrypted and accessed by Bob, the only person with the associated private key.
With this asymmetric encryption method, parties can communicate securely without having first to share a secret key.
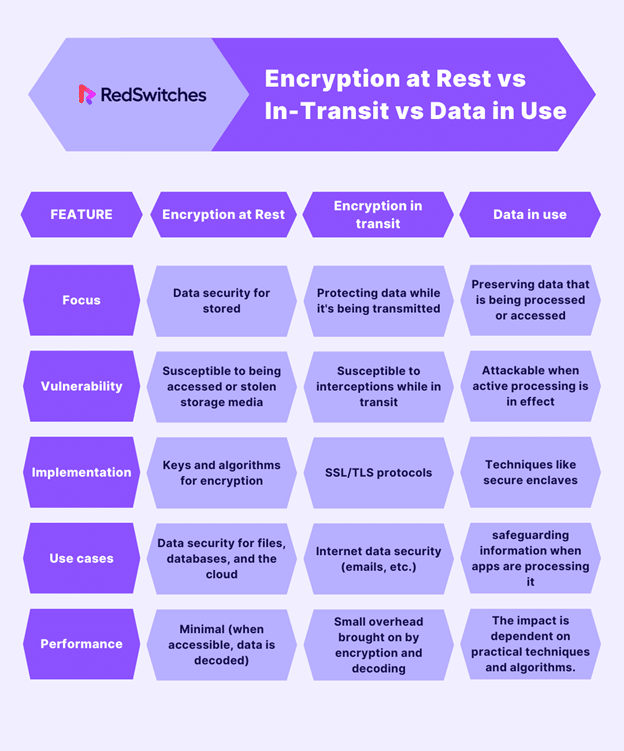
Encryption at Rest vs In-Transit vs Data in Use
First, we will start with the definitions of all three, and then, through a tabular format, we will draw the differences between them.
-
Encryption In-Transit
Data actively being moved from one place to another, such as via the Internet or a private network, is called data in transit or motion.
Effective data protection measures for in-transit data are essential because data is frequently regarded as less secure while in motion. Data protection in transit protects this data while it travels from network to network or is transferred from a local storage device to a cloud storage device.
-
Encryption at Rest
Data at rest is information not actively being sent between networks or devices, such as information archived/saved in some other manner or stored on a hard drive, laptop, or flash drive.
Any information businesses retain for themselves is likewise more valuable in the eyes of hackers, making it a target for outside assaults. Any information archived in a database or kept on a hard disc, computer, or personal device is considered data at rest.
-
Encryption in Use
When a worker or business application accesses or consumes data, it is said to be in use. Data is most vulnerable while being read, processed, or manipulated since it is directly available to a person, leaving it exposed to attack or human error, both of which can have serious repercussions.
Data in use must be encrypted to be protected, and many firms may fortify their encryption systems with extra security precautions like authentication and access rights.
| Encryption at Rest | Encryption in transit | Data in use | |
| Focus | Data security for stored | Protecting data while it’s being transmitted | Preserving data that is being processed or accessed |
| Vulnerability | Susceptible to being accessed or stolen storage media | Susceptible to interceptions while in transit | Attackable when active processing is in effect |
| Implementation | Keys and algorithms for encryption | SSL/TLS protocols | Techniques like secure enclaves |
| Use cases | Data security for files, databases, and the cloud | Internet data security (emails, etc.) | safeguarding information when apps are processing it |
| Performance | Minimal (when accessible, data is decoded) | Small overhead brought on by encryption and decoding | The impact is dependent on practical techniques and algorithms. |
Types of Data at Rest Encryption
Credits: Freepik
Four types of data-at-rest encryption are available for use by businesses:
- Application Level Encryption
At client workstations or server hosts, the application that generates or alters data also executes encryption. The encryption process can be perfectly tailored for each user depending on their responsibilities and permissions using this sort of encryption.
For instance, sensitive client information like contact information or financial records can be encrypted using a cloud-based customer relationship management (CRM) system.
Different encryption techniques are available for each user’s data, guaranteeing that only people with the proper authorization can access particular data bits. Granular control is provided by this method, which is very beneficial for applications handling various and delicate data kinds.
- Database Encryption
The security team encrypts the entire database (or some of it) to protect the files.
For instance, at a financial institution, the entire database of customer transaction records may be encrypted. Without the encryption keys, even if a bad actor were to get access to the database, the data would be inaccessible.
Database encryption is a crucial procedure for companies working with vast volumes of sensitive data since it ensures complete protection for stored data.
- File System Encryption
An administrator can use this type of encryption to encrypt particular file systems (or folders inside a file system). Anyone can start the device with this encryption, but a passphrase is needed to access the protected file systems.
For instance, a business might encrypt private project files in a network-shared folder. The files would remain encrypted and unavailable without the proper credentials in the event of unauthorized access, preserving data confidentiality.
Data saved in various files and directories on servers or local workstations can be secured with the help of file system encryption.
Importance of Data at Rest Encryption
Data Encryption at rest is a necessary component of any comprehensive data protection strategy. Encryption should be used to safeguard sensitive at-rest data since it:
- Prevents unauthorized access to sensitive data from both within and outside the organization.
- Stops an unauthorized person from quickly locating, analyzing, and taking valuable data.
- Limits the attack’s explosion radius if it is successful.
- Safeguards the company if a storage device is stolen or lost.
- Prevents efforts at blackmail after data exfiltration.
- Complying with legal standards can be made more accessible by encrypting data at rest. Two laws that need strong at-rest encryption are the Payment Card Industry( Credit, Debit) Data Security Standard (PCI) and the act commonly known as the Health Insurance Portability and Accountability Act (HIPAA).
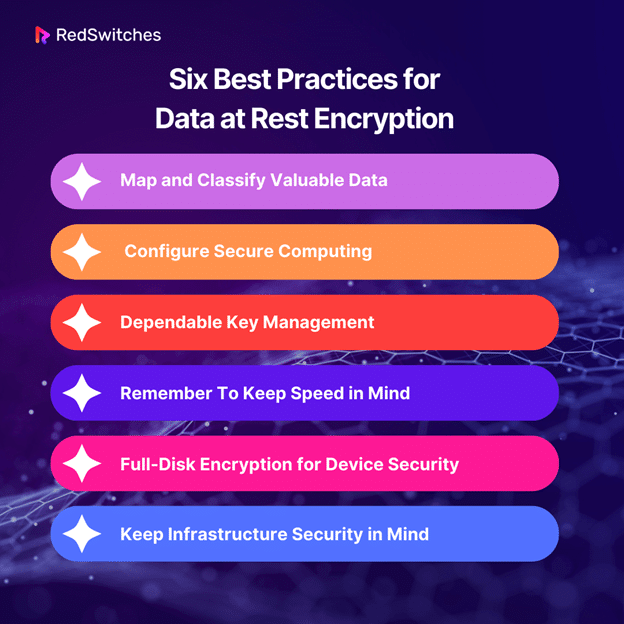
Six Best Practices for Data at Rest Encryption
The recommended Six best practices for developing, implementing, and administering an organization’s data at rest encryption strategy are listed below.
1) Map and Classify Valuable Data
The Primary practice for data at rest encryption is to map your most critical customer and company data before implementing encryption at rest (or any other security method). Businesses classify data differently, but this is a great place to start:
- The importance of each piece of information you have.
- The kinds of data that your company retains.
- The location of essential data in the digital world.
- Where all storage units are located on a physical level.
- All people, programs, and devices have access to private information.
This analysis aids in determining which files don’t need as much security and which data needs encryption. With this knowledge, you can begin developing your encryption strategy and coordinating your efforts with your company’s unique requirements and use cases.
2) Configure Secure Computing
The second practice for data at rest encryption is that Confidential computing should be considered if your company uses cloud services and wants to secure data. End-to-end data security is ensured by this new paradigm for cloud security, which adds data in-use protection to at-rest and in-transit encryptions.
Confidential computing lowers the danger of a compromise or leak even further by encrypting workloads as they are processed. The following are some of the primary advantages of this tactic:
- Encrypting data over its entire lifespan.
- Narrows the attack surface.
- Reduced threat from both insiders and outsiders.
- Increased openness and improved environmental controls.
- Enhanced security in multi-cloud configurations.
3) Dependable Key Management
When implementing data at rest encryption, you must know that Only your crucial management can ensure the security and dependability of your encryption scheme. The following key management best practices should be used to keep keys secure at all stages of their lifecycle (creation, storage, use, maintenance, and deletion):
- Never keep the decryption key and the encrypted data in the exact location.
- Use various keys for various systems and subsystems.
- Keep your keys updated.
- Never utilize keys that have already been used.
- To keep keys secure, use zero-trust security.
- Keep your keys in a hardware security module (HSM).
4) Remember To Keep Speed in Mind
Encrypting all of your organization’s data is not a good idea. It takes a lot longer to decrypt data than it does to access plaintext data. A surplus of cryptography can
- Scale back on the action.
- Performance of the app.
- Make routine chores exceedingly tricky.
- Seriously hinders team agility and business scalability.
To prevent performance concerns, keep the quantity of data you encrypt to a minimum. You can employ selective encryption of database fields (or rows or columns) rather than encrypting all data, for instance, if a database contains sensitive data and non-critical files. This is a very important strategy for data at rest encryption.
5) Full-Disk Encryption for Device Security
Although app, file, and database-level encryption have their purposes, it is the safest course of action to rely on complete disc encryption.
The most secure method is full disc encryption, which safeguards data even if a device containing confidential information is stolen or lost. If your firm uses BYOD (Bring Your Own Device) regulations, the requirement for full-disk encryption becomes even more crucial.
6) Keep Infrastructure Security in Mind
Data encryption at rest is only as safe as the system that enables it. Make sure the group patches all pertinent software appropriately.
- Networking services, including wireless protocols, satellite, DSL, and IP addresses.
- Running programs.
- Network software (both local and cloud-based).
- Network security applications.
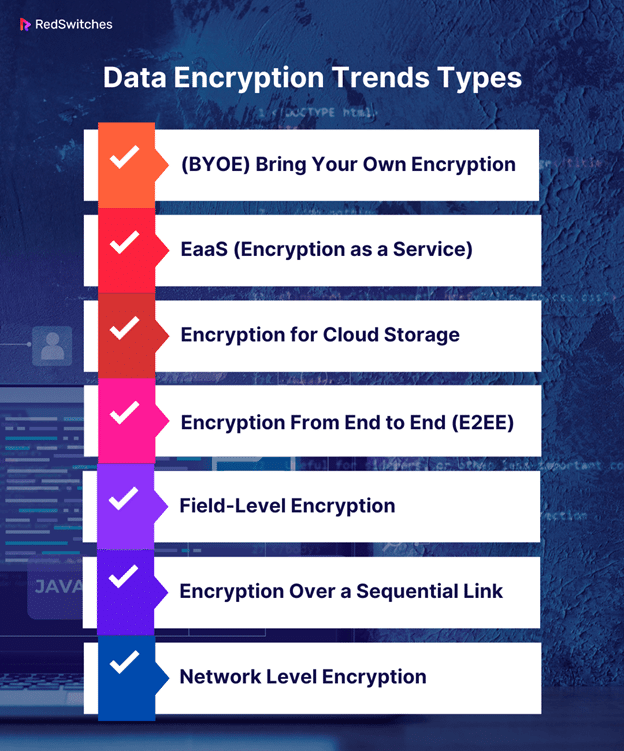
Data Encryption Trends Types
Here are a few trends that will probably influence how data encryption develops in the future:
- (BYOE) Bring Your Own Encryption
A BYOE security architecture for cloud computing enables users of cloud services to control their own encryption keys and encryption software. BYOK, or bring your own key, is another name for it. Customers can install virtualized instances of their own encryption software alongside cloud-hosted business apps using BYOE.
- EaaS (Encryption as a Service)
Pay-per-use encryption is a service cloud providers provide under the EaaS subscription model. In addition to addressing regulatory issues, this method gives clients some control over managing their encryption to protect data in multi-tenant setups.
- Encryption for Cloud Storage
A service in which cloud storage providers encrypt all data before it is saved to the cloud. On-premises encryption is comparable to this, but there are some key distinctions. To match the level of confidentiality of their self-managed encrypted data, cloud clients should try to learn the provider’s rules and practices around encryption and key management.
- Encryption From End to End (E2EE)
E2EE guarantees that an attacker who spies on a communication channel cannot view the data sent between them. Attackers can access content before and immediately after it is decrypted by the server when Transport Layer Security (TLS) provides an encrypted route between web clients and servers.
- Field-Level Encryption
The ability to encrypt data in particular fields on a web page, like credit card numbers, social security numbers, bank account numbers, and health-related information, is known as field-level encryption.
- Encryption Over a Sequential Link
Data is encrypted as it leaves a host, decrypted on the following network connection (a host or a relay point), and then encrypted once more before being sent to the following link. The data is encrypted at each link using a different key or method, and the process is repeated until the data reaches the receiver.
- Network Level Encryption
By using this technique, network forwarding layer (level 3 in the OSI model) cryptographic services are applied. This is situated below the application layer and above the data link layer. Internet Protocol security (IPsec) is used to accomplish Level 3 encryption. It develops a foundation for private communications in IP networks when combined with some IETF standards.
Conclusion
In the current digital environment, it is crucial to comprehend the importance of data at rest encryption. We examined the core ideas behind data encryption, separating it from data in use and transit.
We’ve emphasized the value of robust encryption techniques to protect sensitive information by reviewing the six best practices. Keeping up with the most recent encryption techniques and kinds is essential to maintaining a safe data environment as technology advances.
RedSwitches is a crucial ally in this era of cyber threats by providing cutting-edge solutions to strengthen data protection. Organizations can strengthen their defenses by adopting encryption at rest, guaranteeing that data is inaccessible to unauthorized parties even when kept.
Remember, knowledge and proactive steps are essential in data protection. We are at the forefront, enabling businesses to enter the digital world with security and assurance.
FAQs
Q. What is the best encryption for data at rest security?
AES (Advanced Encryption Standard) is generally considered a solid option, although the optimum encryption for data at rest depends on the specific circumstances.
Q. What is an example of data at rest security?
Encrypting files on a computer’s hard drive with programs like BitLocker for Windows or FileVault for macOS is an example of data at rest encryption.
Q. How to encrypt data at REST API?
The HTTPS protocol allows for data at rest protection APIs, ensuring a secure connection between clients and servers.
Q. What is data at rest encryption and in transit?
Data encryption at rest secures data while it is being stored, whereas data encryption in transit safeguards data while it is being sent. Both strategies provide complete security.
Q. What are the three different encryption methods?
Symmetric encryption, asymmetric encryption, and hashing algorithms are the three different encryption techniques, and each has a specific function in data protection.