There are a few different way’s to update to vCenter server appliance (VCSA). In this post we will be going through using CLI method to apply vCenter patches. Before updating VCSA make sure you have a current backup and take a snapshot before proceeding in case of any issues with the update.
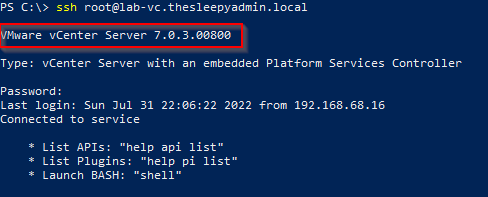
First we need to connect to the vCenter server using SSH. I will be using the inbuilt OpenSSH feature in PowerShell but you can use what ever SSH client you prefer.
To enable SSH on vCenter logon to the management page using the vCenter URL with port 5480 (https://vcenter.domain.local:5480).
Go to Access and click edit to enable SSH Login.

Next we need to connect to the vCenter server using ssh.

Next we can run the below command to view the vCenter update history
software-packages list --history
We can use the below command. This will list the current update settings, if the vCenter server has no internet access then you could update the URL to use an internal web site that contains the update files.
update.get
We will be using the default URL from the update.get command when running the update
software-packages install --url https://vapp-updates.vmware.com/vai-catalog/valm/vmw/8d167796-34d5-4899-be0a-6daade4005a3/7.0.3.00100.latest/ --stage --acceptEulasThis command will download, stage the update and install.

Once stage the update will then start to install.
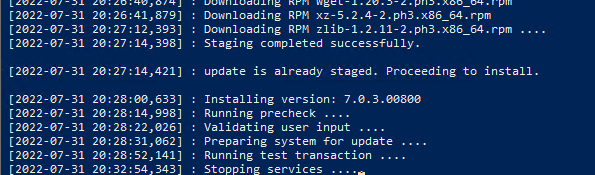
The update can take awhile to complete.

Once the update has completed, vCenter should reboot if required to complete the install.
When the appliance boots backup we can re-connect to confirm we are now running on the updated VCSA version.